Protecting Cloud Data with Encryption Techniques
In today’s digital landscape, the use of cloud computing has become prevalent for individuals and businesses alike. However, the security of cloud data remains a significant concern. Protecting sensitive information from unauthorized access and data breaches is paramount. One of the most effective ways to safeguard cloud data is through advanced encryption techniques. This article will explore the importance of cloud data protection and delve into various encryption methods that can be employed to ensure data security.
Importance of Cloud Data Protection
Cloud data protection is crucial due to the sensitive nature of the information stored in the cloud. Whether it’s personal data, financial records, or proprietary business information, unauthorized access to this data can lead to severe consequences, including identity theft, financial loss, and reputational damage. Employing robust encryption techniques adds an extra layer of security, making it significantly harder for malicious actors to compromise the data.
Understanding Encryption
Encryption is the process of converting readable data into an encoded format that can only be accessed with the correct decryption key. It ensures that even if the data falls into the wrong hands, it remains unintelligible and unusable. Encryption algorithms use complex mathematical formulas to scramble the data, rendering it meaningless without the appropriate key.
Common Encryption Techniques
3.1. Symmetric Encryption
Symmetric encryption, also known as secret key encryption, uses a single key to both encrypt and decrypt the data. The same key is shared between the sender and the recipient, making it essential to keep the key secure. Symmetric encryption is fast and efficient, but the challenge lies in securely distributing and managing the encryption key.
3.2. Asymmetric Encryption
Asymmetric encryption, or public-key encryption, utilizes a pair of keys: a public key and a private key. The public key is freely available and used for encryption, while the private key is kept secret and used for decryption. Asymmetric encryption eliminates the need to securely share a single key but is computationally more intensive.
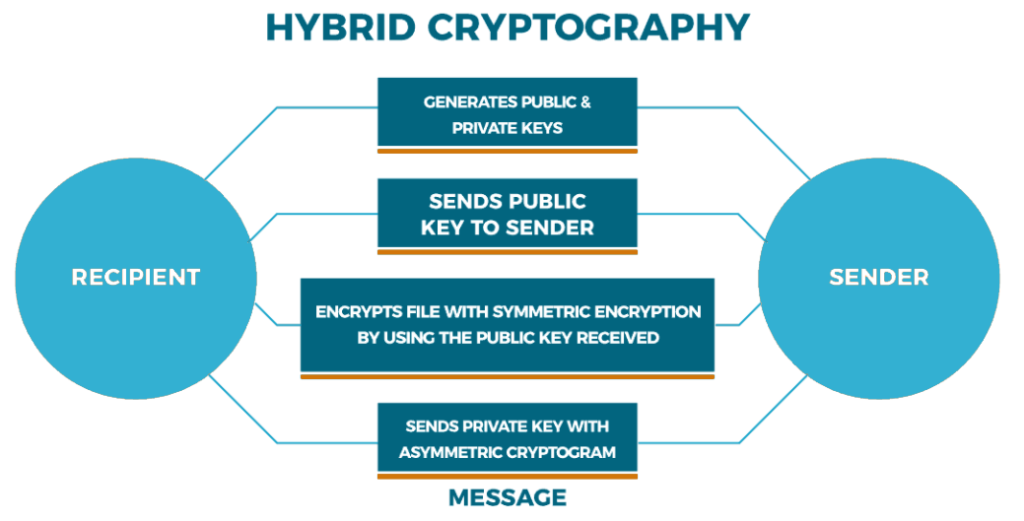
3.3. Hybrid Encryption
Hybrid encryption combines both symmetric and asymmetric encryption to leverage their respective advantages. In this approach, a symmetric key is generated for encrypting the data, and then the symmetric key itself is encrypted using the recipient’s public key. This combination ensures both speed and security.
Advanced Encryption Techniques
4.1. Homomorphic Encryption
Homomorphic encryption is a cutting-edge technique that allows computations to be performed on encrypted data without decrypting it. This unique property enables data to remain protected even during processing or analysis, making it highly valuable for cloud environments where data needs to be accessed and manipulated without exposing its contents.
4.2. Zero-Knowledge Proof
Zero-knowledge proof is a cryptographic method that enables one party to prove knowledge of specific information to another party without revealing the actual information itself. It provides a way to authenticate or verify data without sharing sensitive details. Zero-knowledge proof enhances the privacy and security of cloud data, as it allows users to prove their credentials or access rights without disclosing the underlying information.
4.3. Quantum Encryption
Quantum encryption leverages the principles of quantum mechanics to provide unbreakable encryption. It utilizes the unique properties of quantum particles to encode and transmit data securely. Quantum encryption offers robust protection against sophisticated attacks, including those leveraging quantum computing. Although still in its early stages, quantum encryption shows great promise for securing cloud data in the future.
Implementing Encryption in Cloud Environments
5.1. Encryption at Rest
Encryption at rest focuses on protecting data while it is stored in the cloud. When data is not actively being accessed, it should remain encrypted to prevent unauthorized access. This can be achieved by encrypting the entire storage system or specific files and databases.
5.2. Encryption in Transit
Encryption in transit ensures that data remains secure while being transmitted between the user’s device and the cloud server. This is commonly achieved using protocols like SSL/TLS, which encrypt data during transmission, making it unreadable to eavesdroppers or attackers.
5.3. Key Management
Proper key management is vital for effective encryption in cloud environments. It involves securely generating, storing, distributing, and revoking encryption keys. Robust key management practices include using strong encryption algorithms, regularly rotating keys, and implementing access controls to prevent unauthorized key access.
Challenges and Considerations
Implementing advanced encryption techniques in cloud environments comes with challenges. These include the computational overhead of certain encryption methods, the complexity of key management, and compatibility with existing cloud infrastructure. It is crucial to evaluate these factors and select encryption solutions that strike the right balance between security and performance.
Benefits of Advanced Encryption
Employing advanced encryption techniques for cloud data protection offers several benefits. It safeguards sensitive information from unauthorized access, reduces the risk of data breaches, and helps organizations comply with regulatory requirements. Encryption also enhances trust and confidence in cloud services, enabling businesses and individuals to leverage the benefits of the cloud without compromising security.
Conclusion
Protecting cloud data with advanced encryption techniques is essential to ensure the confidentiality, integrity, and availability of sensitive information. By understanding encryption methods, such as symmetric, asymmetric, and hybrid, as well as advanced techniques like homomorphic encryption, zero-knowledge proof, and quantum encryption, organizations can implement robust security measures. Encryption at rest, encryption in transit, and proper key management play vital roles in securing data within cloud environments. Despite the challenges, the benefits of advanced encryption are undeniable, providing peace of mind and maintaining the privacy of cloud-stored information. Take the Next Step! Please call 866.421.9522 to schedule a meeting with one of our industry experts.
USAccess LLC
Copyright © 2023. All Rights Reserved
